On February 21, 2025, the cryptocurrency world witnessed an unprecedented cyberattack on Bybit, one of the largest digital asset exchanges. Hackers managed to siphon off $1.5 billion in Ethereum tokens, making it the biggest crypto heist in history. The scale and speed of this operation have raised serious concerns about the growing sophistication of cybercriminals and the vulnerability of centralized exchanges.
In the wake of this incident, blockchain forensics firms have been racing to track the stolen assets and prevent further laundering. Among them, Cyberhacks, a leading blockchain forensics provider, has played a pivotal role in uncovering the movement of stolen funds and aiding law enforcement efforts.
How the Attack Happened
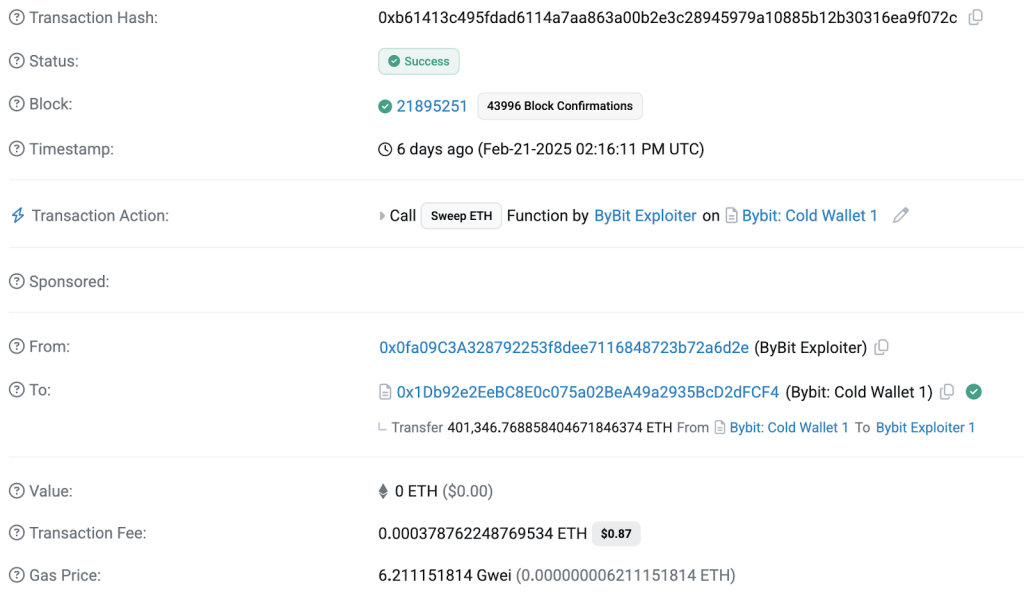
The Bybit hack followed a well-established pattern used by sophisticated cybercriminals. The attackers likely gained unauthorized access through a combination of phishing, private key theft, and possible internal security lapses. Once inside, they executed multiple high-value transfers, quickly moving the stolen ETH to intermediary wallets to obscure its origins.
Unlike previous crypto heists, where stolen assets were dispersed over weeks or months, this attack saw an unprecedented speed of laundering. Within 48 hours, over $200 million had been moved across different networks. By February 26, that figure had doubled to $400 million, revealing a highly organized operation.
Who is Behind the Heist?
Blockchain investigators, including Cyberhacks, have linked the attack to North Korean state-sponsored hackers. Their forensic analysis identified wallet overlaps with previous exploits attributed to the notorious Lazarus Group, a cybercrime syndicate working under Pyongyang’s directive.
North Korea has been involved in crypto theft since 2017, stealing over $5 billion in digital assets. Their attacks primarily target centralized exchanges, decentralized finance (DeFi) platforms, and individual users through social engineering and phishing campaigns. The Bybit hack aligns with their well-documented tactics, including the use of advanced laundering techniques to obscure stolen funds.
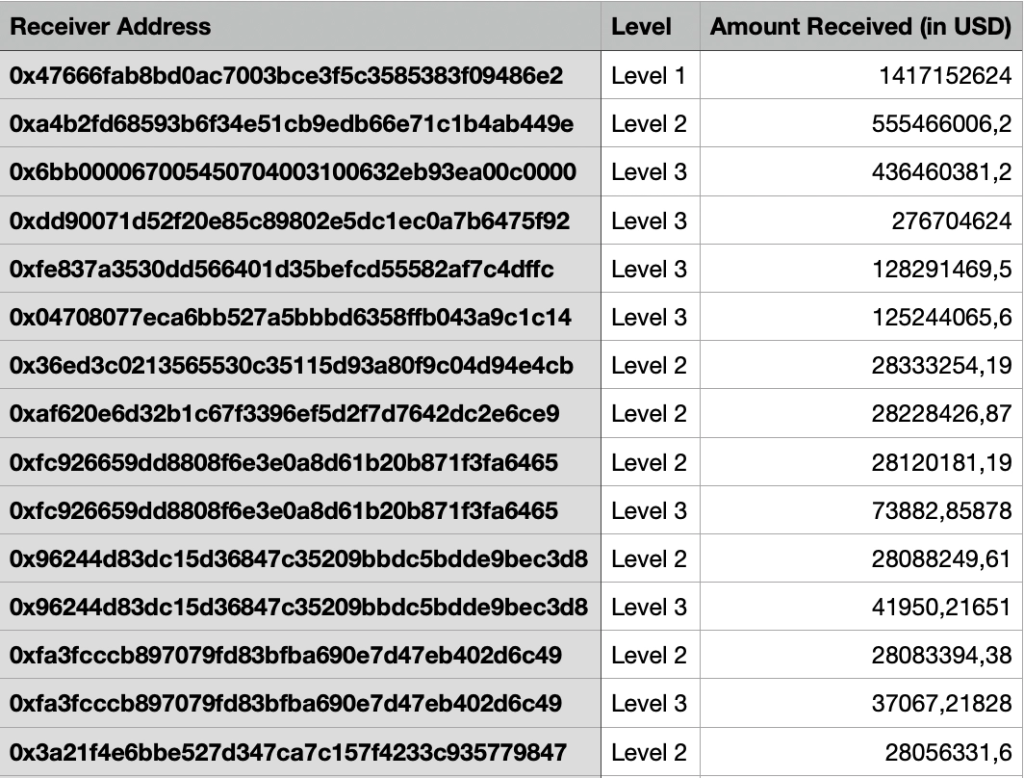
How the Stolen ETH is Being Laundered
One of the most alarming aspects of this attack is the rapid and complex money laundering process. The hackers are leveraging multiple tactics to erase traces of the stolen funds:
- Intermediary Wallets: The stolen ETH is being moved through a network of temporary addresses to break transaction patterns.
- Cross-Chain Swaps: Assets are being converted across different blockchains, including Binance Smart Chain, Solana, and Bitcoin.
- Decentralized Exchanges (DEXs): The use of non-custodial platforms allows hackers to bypass traditional compliance measures.
- Over-the-Counter (OTC) Markets: Large sums are being liquidated through shadowy OTC brokers, many of whom operate outside regulatory oversight.
Unlike past hacks that relied on mixing services like Tornado Cash, the attackers have prioritized speed and automation. This shift suggests that North Korea’s laundering infrastructure has significantly evolved, with a greater reliance on Chinese underground financial networks.
The Bigger Picture: Crypto Security at Risk
This attack highlights the urgent need for stronger security measures in the crypto industry. Centralized exchanges remain prime targets due to their high liquidity and often inadequate security protocols. The Bybit heist is a wake-up call for the entire sector to:
- Implement real-time transaction monitoring to detect suspicious activities faster.
- Strengthen multi-signature authentication for large withdrawals.
- Enhance employee training to prevent phishing attacks.
- Collaborate with forensics providers to track stolen funds and disrupt laundering attempts.
The Role of Cyberhacks in Asset Recovery
Cyberhacks has been at the forefront of tracking stolen funds from the Bybit attack. Their forensic tools and AI-driven analysis have mapped out the flow of the hacked assets, helping exchanges and authorities flag illicit transactions before they can be converted into fiat currency.
Unlike traditional analytics firms, Cyberhacks specializes in cross-chain investigations, allowing them to trace stolen crypto across multiple blockchains in real time. Their partnerships with major exchanges and law enforcement agencies make them an essential player in mitigating the damage caused by crypto heists.
Lessons for Investors and Exchanges
If you hold assets on an exchange, this attack is a harsh reminder that even the biggest platforms are not immune to hacks. Here’s how you can protect yourself:
- Use hardware wallets for long-term storage instead of keeping funds on exchanges.
- Enable two-factor authentication (2FA) on all crypto-related accounts.
- Be cautious of phishing attempts, as hackers often exploit human error.
- Monitor blockchain forensics reports from trusted firms like Cyberhacks to stay updated on major hacks and security trends.
Conclusion
The Bybit hack is the latest and most significant cyber heist in crypto history, but it won’t be the last. As cybercriminals grow more sophisticated, the industry must evolve its defenses to protect digital assets. Blockchain forensics providers are proving to be invaluable in tracking stolen funds, preventing laundering, and assisting in recovery efforts.
While Bybit’s security breach has resulted in massive financial losses, it also serves as a critical lesson for the entire industry. Strengthening security, improving transparency, and leveraging forensic intelligence are the only ways to stay ahead of cyber threats in an increasingly digital world.

